Posts
349Following
95Followers
3793Greg K-H
gregkhEverything is now public for you to test with, and as always, different workloads have different impacts, so anything I might say, might not be relevant for your usage model at all.
Greg K-H
gregkhGreg K-H
gregkhBut that isn't an acceptable interface for upstream, for all the same reasons :)
Greg K-H
gregkhGreg K-H
gregkhGreg K-H
gregkhI get many "private" emails from companies that do 1-2 month syncs of the LTS branches in their private SoC trees usually saying "all is good!" which gets them into the habit of doing testing. And every once in a while, they do find a regression, which we work quickly to resolve (many times it's just "use the next version, this was already caught...)
So yes, merge with LTS, test, and let me know the results please.
Greg K-H
gregkhGreg K-H
gregkh{sigh}
Greg K-H
gregkhOr to quote someone wise, "Everybody wants progress, nobody wants change."
Greg K-H
gregkhGreg K-H
gregkhJohn did it much better with one less adapter than I so this stack could be smaller if needed, but this is all I could find locally.
Greg K-H
gregkhhttps://kccnceu2023.sched.com/event/1Lnv0
Should be fun, if you are at KubeCon, stop by and ask questions, it's meant to be a discussion. A recording will be made public afterwards too.
Greg K-H
gregkhbpftrace fun question of the week I’ve been beating my head against for a while now.
Given the following bpftrace program:
tracepoint:syscalls:sys_enter_open,
tracepoint:syscalls:sys_enter_openat
{
$g = "magic_command_to_exit_trace";
$s = str(args->filename);
printf("%s\n", $s);
if ($s == $g) {
exit();
}
}
I get the lovely warning:
WARNING: Addrspace mismatch
if ($s == $g) {
which I can understand. But what I can’t figure out is how to resolve this (hint, the program works just fine, when opening the “magic” file, the trace exits), as how to turn a literal string into the proper address space that args->filename is?
I’ve dug into too many bpftrace git commits to try to figure it out, to no luck. Anyone have a hint?
Oh, and if you want to see where this is used, it’s in this “fun” script: https://github.com/gregkh/gregkh-linux/blob/master/scripts/trace_kernel_build.sh
Warning, realpath takes a long time when processing millions of files, be patient when running the script.
Greg K-H
gregkhGreg K-H
gregkhGreg K-H
gregkhhttps://social.kernel.org/notice/AU5IphRPUsQvvkx732
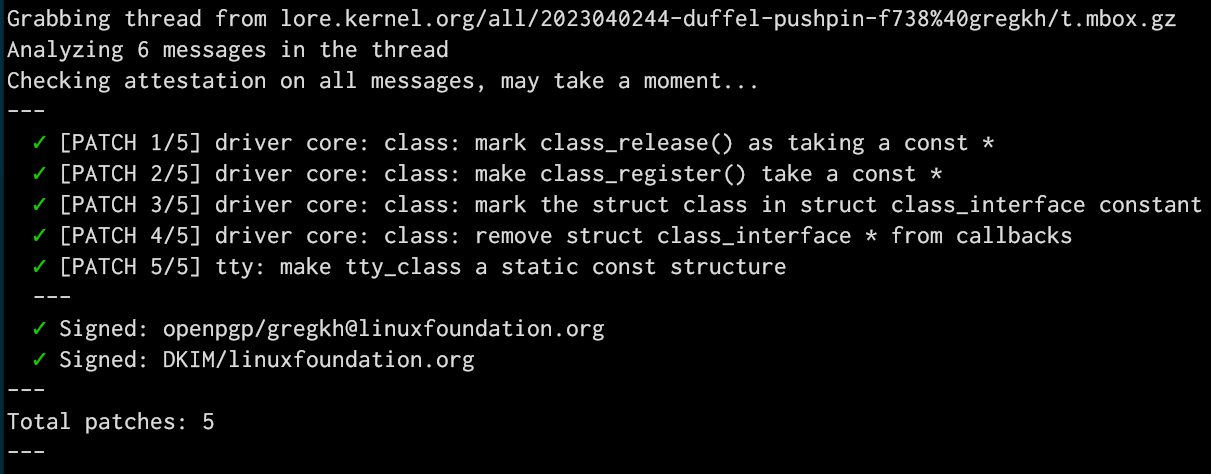
But why does any of this matter? As most everyone knows, Linux kernel development happens through email, and the Message-Id of an email is a unique identifier that is used to track messages in our patch handling tools and archives (see https://lore.kernel.org for the archives.) By crafting shorter-but-still-unique message ids it's easier to reference those messages in other places, and using words is just prettier overall than random UUID values (https://i.redd.it/64gl4t9s52ra1.jpg for an example)
Bonus to all of this is that people don't realize that most of the patches we send out are actually signed and can be validated as coming from the person that sent them. The tool we use for that looks at the body of the email, and a small subset of the Header tags in the email. By providing to the tool our custom Message-Id, that adds yet another portion of the email that is now able to be signed and validated, providing a tiny bit more security overall in the patch submission processes (very very tiny, I know, but it's real, as I found out when I submitted a patch with a broken message-id from what was signed and our tools caught it.)
Anyway, all of that is a long way of showing off a tiny core change to the kernel that allows some core structures to be moved to read-only memory that I've been working on for a few months now. Here's the last portion of that work being sucked off of the email archives and validated as coming from me:
Greg K-H
gregkhOk, all now working properly, and bonus, the message-id is now part of the signature on the email itself!