Posts
350Following
95Followers
3920jelly
jelly@dodgy.downloadNew blogpost about creating bit-by-bit reproducible images with mkosi(!)
https://vdwaa.nl/mkosi-reproducible-arch-images.html
#archlinux #systemd #mkosi
K. Ryabitsev-Prime 🍁
monsieuriconMe: "Oh, yeah, for sure."
Greg K-H
gregkhGreg K-H
gregkh? No need even for shim!
Greg K-H
gregkhAnd it's nice to see we aren't alone here with "big numbers", it's going to be an interesting thing to watch shake out as "take responsibility" rules/laws come into being in different locations. I agree with you in that the quantity is just going to get larger over time.
Greg K-H
gregkhKernel source is all public (there's a 6.1.y and 6.6.y tree at the moment), hopefully will start working on getting it all merged upstream to make it a proper platform for others to use.
Greg K-H
gregkhGreg K-H
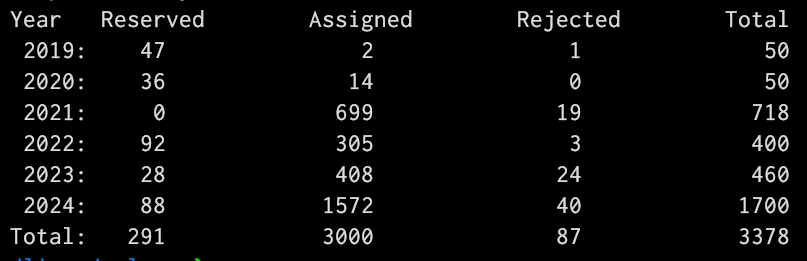
gregkhSorry to nit-pick, just wanted to be specific as 3000 in 6 months originally seemed like a lot to me before I went back and looked at these numbers.
Also, for those who want to play along on their own, just clone our vulns.git repo at git.kernel.org and look at the information directly there yourself, it's all being reviewed and assigned in the open, unlike other projects...
Greg K-H
gregkhGreg K-H
gregkhGreg K-H
gregkhSo there is no benefit or need to be "private" about tagging specific commits as CVEs before we do so as you should have already taken all of these fixes weeks ago anyway.
Greg K-H
gregkhYes, once we agree "this commit should get a CVE" we have tools to make the assignment and publish the notice in an automated way, but all CNAs have something like that (if they don't they are wasting a lot of time doing it by hand.)
Thorsten Leemhuis (acct. 1/4)
kernellogger@fosstodon.orgI'd really like to read a well researched article that sums up how Linux distros reacted to the massive influx of #Linux #kernel CVE that started ~half a year – both for their #LinuxKernel packages and their live-patching offerings.
But I guess that is an enormous amount of work that no media outlet in this world is willing to pay anyone for writing. 😕
Slide taken from @gregkh's "Why are there so many kernel CVEs?" talk he gave at OSS China yesterday (https://social.kernel.org/objects/c9979d9f-399f-428b-ac56-c41598076dfa ) #LinuxKernel
sjvn
sjvn@mastodon.socialDon't panic! It's only 60 Linux CVE security bulletins a week https://zdnet.com/article/dont-panic-its-only-60-linux-cve-security-bulletins-a-week/ by @sjvn
Sure, it sounds like a lot, but it's just business as usual for #Linux #security.
Greg K-H
gregkhHere's a good summary of the talk from @sjvn : https://www.zdnet.com/article/dont-panic-its-only-60-linux-cve-security-bulletins-a-week/
Greg K-H
gregkhhttps://kccncossaidevchn2024.sched.com/event/ed2b39a9a0cdfc1df18de67ce0c2f6be
Link to git repo for the slides if the schedule site acts odd for you:
https://git.sr.ht/~gregkh/presentation-security
It was fun, and will be the "set up" for my Kernel Recipes talk in Paris in a few weeks (only 3 conferences to go between now and then, travel is back in full swing.)
pabloyoyoista
pabloyoyoista@social.treehouse.systemsOk, so the day has come. On the context of getting "/usr merge" on alpine, I am going to try update the FHS.
9 years after it was updated, big parts of it are out-of-sync with the current Linux distro conventions.
We (@postmarketOS) already pinged the @linuxfoundation about it in February, and their suggestion was to get somebody interested to do the work. So let's start that process now! Since the FHS mailing list seems defunc (I subscribed and sent an email in February that never got added to the archive), please send me an email at pabloyoyoista@postmarketos.org so we can get a list of people to start discussing the process
#linux #distros #debian #fedora #alpinelinux #postmarketOS #systemd
bert hubert 🇺🇦🇪🇺🇺🇦
bert_hubert@fosstodon.orgRecently, a Dutch hacker found a vulnerability allowing him to shut down 4 million solar power installations. A handful of mostly non-European places manage perhaps 100 GW of solar power in the EU. Any mishap there, or heaven forbid, a compromise, could easily shut down so much power that the European electricity grid would collapse. Shockingly, we regulate these massive control panels as if they are online birthday calendars. And that must change. https://berthub.eu/articles/posts/the-gigantic-unregulated-power-plants-in-the-cloud/