Posts
350Following
95Followers
3794Krzysztof Kozlowski
krzkEOSS: https://sched.co/1aBEf
OSSNA: https://sched.co/1aPvr
Greg K-H
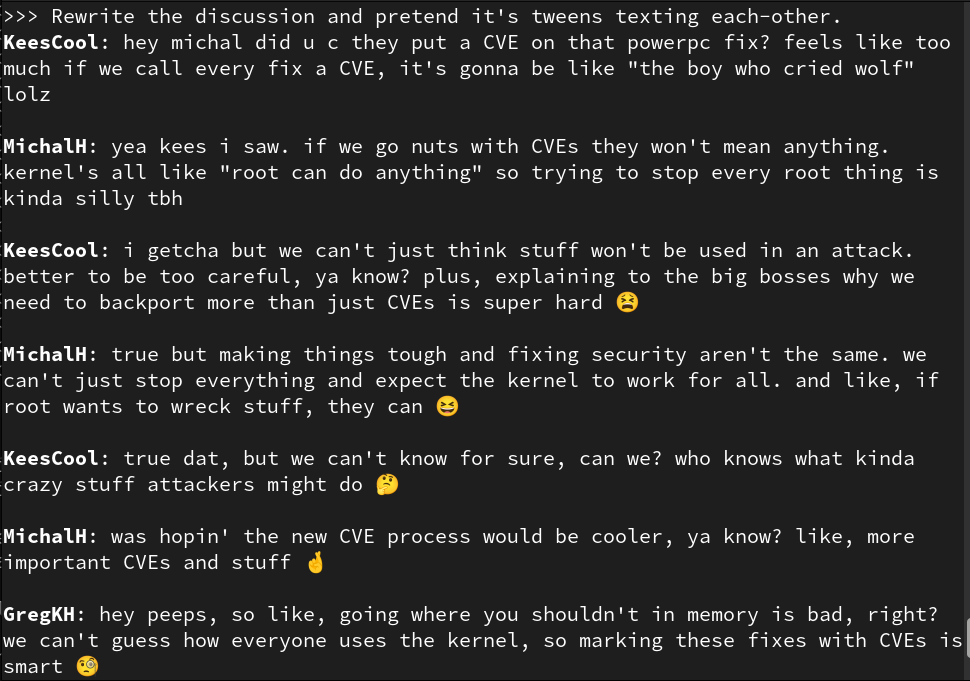
gregkhNow when stable releases happen, we go and updated all existing CVEs to add the needed information where the fix has landed in stable kernels, and push the updates to the cve.org website in json format.
So for CVE-2024-26653, on the cve.org site, you will see that the latest stable info is included, while the older email link you provided, only says that the -rc2 is covered. But if you look in the git archive, the mbox announcement is now updated: https://git.kernel.org/pub/scm/linux/security/vulns.git/tree/cve/published/2024/CVE-2024-26653.mbox
Such is the lifecycle of a kernel change, they get backported all the time...
Thomas Depierre
Di4na@hachyderm.ioWell, I finally have data to back my model of the software world out there. And the data is relatively solid and shows what I keep saying.
You are all on our turf now. Please accept that you have no idea what you are talking about. Sit down. Listen. Ask questions.
But respect our work. We are trying to keep the world running, 1h per month.
https://www.softwaremaxims.com/blog/open-source-hobbyists-turf
LWN.net is now @LWN@lwn.net
LWN@fosstodon.orgEight new stable kernels https://lwn.net/Articles/966755/ #LWN
Greg K-H
gregkh:)
Any job that asks you that type of question is just trying to mess with the applicants, stay away from that type of place as much as possible.
mhoye
mhoye@mastodon.social@drewdevault I think I can save you a step here, we did a research paper on this a few years ago.
"Do Software Developers Understand Open Source Licenses?"
https://www.cs.ubc.ca/~murphy/papers/licensing/software-licensing.pdf
To my chagrin my co-authors overruled me, but in my first draft the abstract was just:
"Nope."
Tweakers
Tweakers@mastodon.socialMinister Adriaansens: verhuizing SIDN naar Amazon 'nog geen voldongen feit' https://tweakers.net/nieuws/220102/minister-adriaansens-verhuizing-sidn-naar-amazon-nog-geen-voldongen-feit.html
Greg K-H
gregkhLinux Kernel Ecosystem" in which different distros, and Android, are evaluated as to how up to date they stay with upstream fixes. Note that RHEL or CentOS is not evaluated "because of the lack of public git repositories or insufficient data."
About time someone started writing papers about this stuff...
Palmer Dabbelt
palmerOmkhar
Omkhar@infosec.exchangeWe're #hiring at the @openssf !
Our mission is to ensure the security of open source software for all.
Are you a seasoned Technical Program Manager excited about #cybersecurity and #opensource who wants a full-time #remotejob?
Apply: https://openssf.jobboard.io/jobs/314008394-technical-program-manager-at-openssf
Greg K-H
gregkhTo quote Ben Hawks, "It's hard to capture the fact that a bug can be super serious in one type of deployment, somewhat important in another, or no big deal at all -- and that the bug can be all of this at the same time. Vulnerability remediation is hard."
His full post is worth reading: https://blog.isosceles.com/what-is-a-good-linux-kernel-bug/
Greg K-H
gregkhThey also asked us to backfill the database with our previously submitted GSD information, as well as everything that gets merged forward. That backfill work is ongoing and is the large volume of what is currently being assigned right now. That information has already been out there for years in GSD, putting it in CVE doesn't change the actual kernel commits or "security" at all, it's just that you might not have noticed the GSD entries (hint, the "bad guys" sure did...)
The number of "new" CVE entries is a small % overall as we really have only processed the changes from v6.7.0..v6.7.3 or so. We are behind in the new stuff and will catch up soon there, help is always appreciated, if you see a commit you want assigned a CVE, just ask!
As others have said, this hasn't changed how the kernel commits are merged at all, it's just calling stuff out that everyone should have already been looking at and merging already, with way more meta-data and information than has ever been done before for kernel CVEs, thereby actually raising the information level in the CVE database here (which is probably why the CVE board wanted this.)
If companies are somehow dictating that they MUST look at and evaluate all CVEs, then they should be happy as many groups were intentionally abusing the CVE process for the kernel previously, making their life much more difficult (including the community's life, which is why we became a CNA.) That abuse has now stopped, to be replaced with a different workflow with way more meta-data produced to help make decisions easier. So far one of the biggest complainers was the company that was doing that abuse as they are no longer allowed to do that (to be specific, that was NOT SuSE).
Greg K-H
gregkhYear Reserved Assigned Rejected Total
2019: 47 2 1 50
2020: 37 13 0 50
2021: 45 205 0 250
2022: 45 5 0 50
2023: 51 145 4 200
2024: 502 48 0 550
Total: 727 418 5 1150
Majority so far is back-filling in from the GSD entries. We've only really done 2-3 stable releases so far, we have a bunch of review to catch up with, you can see the current status in our git repo if people are curious what is being discussed/reviewed.